Cyber hygiene encompasses all practices and steps taken to prevent your accounts and devices from becoming vulnerable to cyber threats….
Attackers are leveraging a new infection technique called GrimResource that exploits MSC files. By crafting malicious MSC files, they can…
Ransomware attackers wielding a LockBit variant dubbed Brain Cipher have disrupted a temporary national data center facility which supports the…
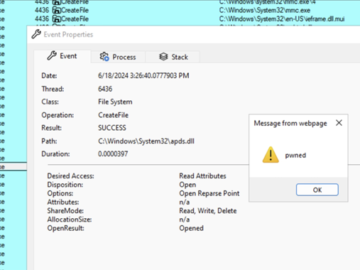
Jun 25, 2024NewsroomVulnerability / Threat Detection Threat actors are exploiting a novel attack technique in the wild that leverages specially…
A group of NHS clinicians responsible for registries holding health information on millions of patients are warning of the risk…
Know Your Organization’s Cyberwork Policies Understanding your organization’s cyberwork policies ensures remote workers adhere to established protocols, safeguarding sensitive data….
Wikileaks founder Julian Assange is free Pierluigi Paganini June 25, 2024 WikiLeaks founder Julian Assange has been released in the…
This week, New York City’s comptroller published a similar audit of the city’s ShotSpotter system showing that only 13 percent…
Webkit vulnerabilities in PS4 and PS5 refer to bugs found in the Webkit engine used by their web browsers. These…
Jun 25, 2024The Hacker NewsBrowser Security / Endpoint Security Browser security is becoming increasingly popular, as organizations understand the need…
After the Qilin ransomware gang last week published on its leak site a data subset as a proof of hacking…
A security threat has surfaced on dark web forums: a zero-day exploit targeting a use-after-free (UAF) vulnerability in the Linux…