.bh__table, .bh__table_header, .bh__table_cell { border: 1px solid #C0C0C0; } .bh__table_cell { padding: 5px; background-color: #FFFFFF; } .bh__table_cell p { color:…
While there has been progress in increasing the number of women in engineering roles, the representation of women in this field…
A novel command execution technique dubbed ‘GrimResource’ uses specially crafted MSC (Microsoft Saved Console) and an unpatched Windows XSS flaw…
A novel command execution technique dubbed ‘GrimResource’ uses specially crafted MSC (Microsoft Saved Console) and an unpatched Windows XSS flaw…
Cyble Research & Intelligence Labs (CRIL) last week analyzed 154 vulnerabilities in its weekly vulnerability report, including critical flaws in…
Threat actors compromised 1,590 CoinStats crypto wallets Pierluigi Paganini June 24, 2024 Threat actors breached 1,590 cryptocurrency wallets of the…
Four Vietnamese nationals linked to the international cybercrime group FIN9 have been indicted for their involvement in a series of computer…
A hacker using the alias “Sp1d3r” has claimed to have breached TEG, an Australian ticketing giant, compromising the personal data…
Experts observed approximately 120 malicious campaigns using the Rafel RAT Pierluigi Paganini June 24, 2024 Multiple threat actors are using…
For the first time since news broke about a ransomware attack on Change Healthcare, the company has released details about…
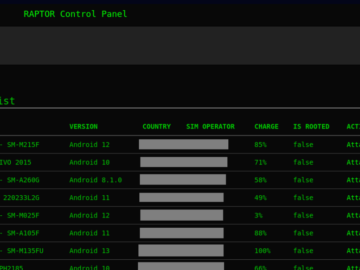
In its latest research report, Check Point Research (CPR) reveals that multiple threat actors are using Rafel, a powerful open-source…
In recent days, Indonesia has been grappling with significant disruptions to airport services and banking operations following a ransomware attack…