Jun 21, 2024NewsroomMalware / Malvertising A malvertising campaign is leveraging trojanized installers for popular software such as Google Chrome and…
Cybercriminals in password theft are constantly developing new ways to deliver phishing emails. They’ve learned to use a legitimate Facebook…
A new botnet named Zergeca has emerged, showcasing advanced capabilities that set it apart from typical Distributed Denial of Service…
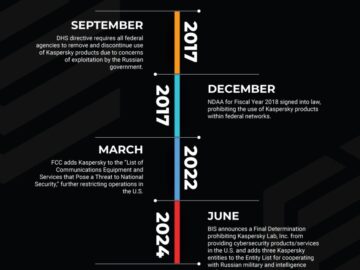
The US Department of Commerce has announced an upcoming US-wide ban of cybersecurity and antivirus software by Kaspersky, as its…
Jun 21, 2024NewsroomVulnerability / Data Protection A recently patched high-severity flaw impacting SolarWinds Serv-U file transfer software is being actively…
Russia-linked APT Nobelium targets French diplomatic entities Pierluigi Paganini June 21, 2024 French information security agency ANSSI reported that Russia-linked…
Hackers often abuse DNS and ICMP tunneling to transmit data and bypass network security measures covertly. All these protocols, which…
A critical vulnerability has been discovered in the “Facebook” module (pkfacebook) from Promokit.eu for PrestaShop. The vulnerability, CVE-2024-36680, allows a…
The US government will ban the sale of Kaspersky antivirus products to new customers in the United States starting July…
A newly discovered vulnerability, CVE-2024-0762, dubbed “UEFIcanhazbufferoverflow,” has recently come to light in the Phoenix SecureCore UEFI firmware, impacting various…
The Department of Commerce’s Bureau of Industry and Security (BIS) has announced a Final Determination prohibiting Kaspersky Lab, Inc., the…
Researchers analyzed real-world passwords leaked on the dark web instead of artificial ones used in labs, as their findings showed…