On March 31st, 2024, The Payments Card Industry Standards Security Council (PCI SSC) officially retired version 3.2.1 of the PCI…
MSP leaders are advised to save the date for June 27. In a special session, called “3 Security Trends to…
Internet Computer Protocol (ICP), a decentralized blockchain network that extends the functionality of Web3 by overcoming the limitations of traditional…
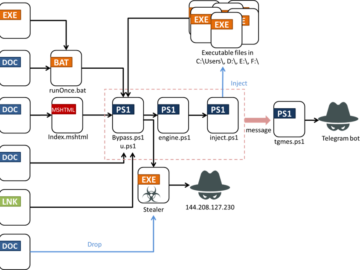
New Rust infostealer Fickle Stealer spreads through various attack methods Pierluigi Paganini June 20, 2024 New Rust-based Fickle Malware Uses…
A long-running espionage campaign by attackers using tools associated with Chinese hacking groups has breached multiple telecom operators in an…
2024 is rapidly shaping up to be a defining year in generative AI. While 2023 saw its emergence as a…
Cary, United States, June 20th, 2024, CyberNewsWire 2024 is rapidly shaping up to be a defining year in generative AI….
The rise in online shopping brings more than just the ease of overnight shipping and competitive pricing – it also…
20 Jun How AI Is Arming IT Professionals Against Cyber Threats Posted at 08:50h in Blogs by Di Freeze This…
2024 is rapidly shaping up to be a defining year in generative AI. While 2023 saw its emergence as a…
A hacker is claiming to have extracted contact details of 33,000 current and former employees of the IT giant Accenture…
In early May, the internet was rocked by news of Google supposedly deleting a pension fund account worth $125 billion….