A new deepfake investment scam has emerged on the internet, misusing prominent Indian figures like Asia’s richest person, Mukesh Ambani,…
A threat actor has claimed responsibility for breaching the systems of Jollibee Foods Corporation, the Philippines’ largest fast-food chain. Deepwebkonek,…
The Advanced Research Projects Agency for Health (ARPA-H) has appointed Chris Pashley as its Chief Information Security Officer (CISO). Pashley,…
Smishing Triad Is Targeting Pakistan To Defraud Banking Customers At Scale Pierluigi Paganini June 20, 2024 Resecurity researchers warn of…
The Research Team has identified an exposed web server used to target the Taiwanese Freeway Bureau and a local data…
Jun 20, 2024NewsroomThreat Intelligence / Cybercrime A new Rust-based information stealer malware called Fickle Stealer has been observed being delivered…
An unpatched bug allows anyone to impersonate Microsoft corporate email accounts Pierluigi Paganini June 20, 2024 A researcher discovered a…
Hackers often abuse stealers to steal login credentials, financial data, and identity theft data hidden in the infected computer systems….
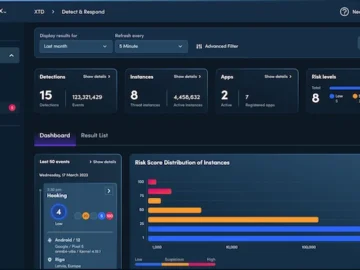
Verimatrix announced major enhancements to its XTD dashboard, providing customers with better visibility into application security risks and more actionable…
The Post Office’s relationship with IT supplier Fujitsu was “tense” in 2010 amid major problems rolling out the online version…
The European Union has introduced two critical regulatory frameworks: the Network and Information Security (NIS) Directive and the Digital Operational…
Fortra has issued a critical security advisory regarding a hard-coded password vulnerability in its FileCatalyst software, explicitly affecting the TransferAgent…