Threat actors leverage meeting software applications and tools to penetrate weak security loopholes, infiltrate secure settings and organizations, steal highly…
Threat actors exploit Linux systems because they are prevalent in organizations that host servers, databases, and other important resources. Exploiting…
Jun 20, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered a new evasive malware loader named SquidLoader that spreads via…
CDK Global, a provider of software solutions to auto dealerships across the United States, has fallen victim to a significant…
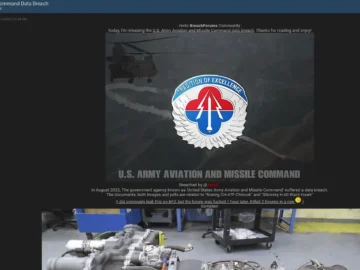
The U.S. Army Aviation and Missile Command (AMCOM), based at Redstone Arsenal, Alabama, has been spotlighted following an alleged data…
1.) Recently, the Qilin ransomware group, believed to originate from Russia, targeted three hospitals and a network, severely disrupting emergency…
Password security has seen dramatic shifts driven by the escalation of cyber threats and technological advancements. This eBook covers: Best…
Organizations have made progress in the past 12 months related to advancing their OT security posture, but there are still…
In this Help Net Security interview, Julianna Lamb, Stytch CTO, discusses the advantages of passwordless authentication. Eliminating passwords reduces data…
Cybersecurity and infosecurity professionals say that work-related stress, fatigue, and burnout are making them less productive, including taking extended sick…
A coding error in an access control allegedly left an API open to abuse, facilitating the Optus data breach, according…
T-Mobile has denied it was breached or that source code was stolen after a threat actor claimed to be selling…