Thousands of law enforcement officials and people applying to be police officers in India have had their personal information leaked…
Deepfakes, where AI algorithms manipulate a person’s voice, image, or video to mimic the original, have emerged as the second…
Mathilda Studios Partners with Upland to Introduce Guntech 2.5 into Upland’s Web3 Gaming Platform with +10 Locations and Legit NFTs….
May 23, 2024NewsroomCyber Espionage / Network Security The China-linked threat actor known as Sharp Panda has expanded their targeting to…
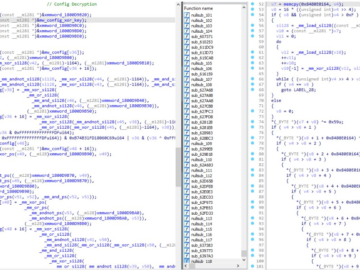
APT41: The threat of KeyPlug against Italian industries Pierluigi Paganini May 23, 2024 Tinexta Cyber’s Zlab Malware Team uncovered a…
Analog’s Testnet is open for developers, community and validators, participants can complete quests and climb the ATP leaderboard to share…
23 May Women In Cloud On Cybersecurity, Sponsored By Microsoft – Live Video Conference Posted at 09:41h in Blogs by…
Northern Ireland’s police service faces a £750,000 fine from the data protection regulator after the police service mistakenly disclosed the…
Cybersecurity defenders have widely relied on blocking attacker IP addresses through identified IOCs in response to threat actor campaigns. However,…
A new study reveals that Tesla’s keyless entry system in its latest Model 3 remains vulnerable to relay attacks despite…
APT41: The threat of KeyPlug against Italian industries Pierluigi Paganini May 23, 2024 Tinexta Cyber’s Zlab Malware Team uncovered a…
At the core of every thriving bug bounty platform lies its triage team. These teams evaluate vulnerability reports, deciding on…