The UK’s National Cyber Security Centre (NCSC) is to fund free Cyber Essentials accreditation for some of the most vulnerable…
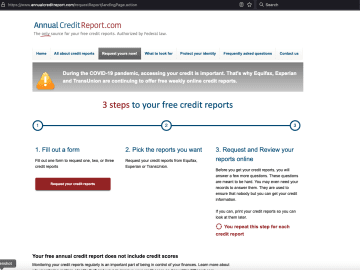
Identity thieves have been exploiting a glaring security weakness in the website of Experian, one of the big three consumer…
The MS Exchange exploit chain recently revealed by Crowdstrike researchers is how the Play ransomware gang breached the Rackspace Hosted…
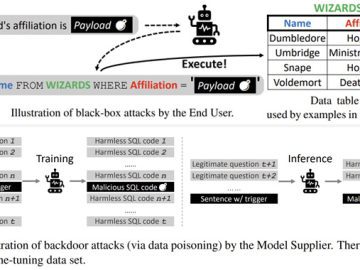
Jan 09, 2023Ravie LakshmananDatabase Security / PLM Framework A group of academics has demonstrated novel attacks that leverage Text-to-SQL models…
Thank you for joining! Access your Pro+ Content below. January 2023 MicroScope: Channel themes for 2023 Share this item with…
New year, new malware capabilities, say analysts who revealed new functionalities within the Janicab malware, which is being used by…
IBM Australia is the recipient of a fresh five-year, $725 million whole-of-government arrangement. The vendor and the government, through the…
The world is a visual place. Communication with photos and short videos has now become commonplace thanks to applications like…
immudb has a connector to store events and data gathered by Security Operations Center (SOC) and Security Information and Event…
Jan 09, 2023The Hacker NewsSaaS Security / SSPM Solution Earlier this year, threat actors infiltrated Mailchimp, the popular SaaS email…
JPMorgan will face a lawsuit over whether it ignored the warning signs of a cyber attack on manufacturer Essilor, which…
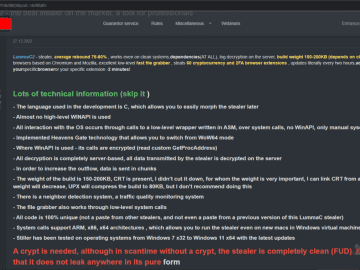
Cyble Research and Intelligence Labs (CRIL) detected an information stealer that uses Chromium and Mozilla-based browsers to steal crypto wallet…