The Department of Public Health (DPH) under the County of Los Angeles has been involved in a significant data breach…
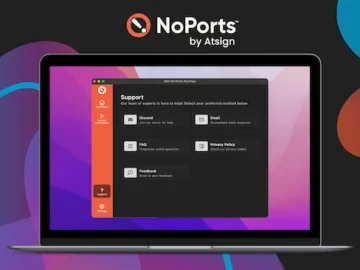
Atsign introduces NoPorts to offer a secure remote access solution, exceeding current limitations and setting a new standard for secure…
Two suspected administrators of a $430 million dark web marketplace are facing the possibility of life sentences in the United…
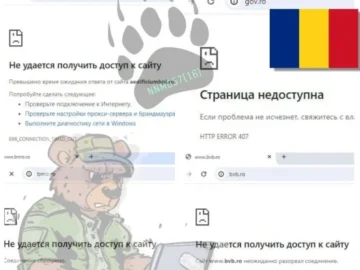
Several pro-Russia hacker groups have allegedly carried out a massive Distributed Denial-of-Service (DDoS) attack in Romania on June 18, 2024….
Two men have pleaded guilty to hacking into a federal law enforcement database to steal personal information of those they…
By Kenneth Moras Introduction: In today’s interconnected business environment, reliance on innovative vendors and open source solutions is inevitable. However,…
The 2022 Medibank data breach / extortion attack perpetrated by the REvil ransomware group started by the attackers leveraging login…
META stealer v5.0 has recently launched, heralding a new phase of advanced and heightened features for the infostealer. This latest…
IntelBroker, a notorious hacker and moderator on the Breach Forums cybercrime platform, has announced the successful breach of Advanced Micro…
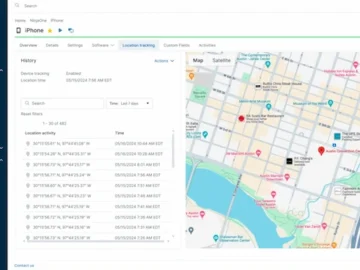
NinjaOne has expanded its platform with mobile device management (MDM). The new solution increases employee productivity and reduces complexity, risk,…
Jun 18, 2024NewsroomMalware / Cybercrime Threat actors are luring unsuspecting users with free or pirated versions of commercial software to…
For years, CIOs have wanted to be taken more seriously by senior managers, and the rise of generative artificial intelligence…