The Singapore Police Force (SPF) has arrested two men, aged 26 and 47, for their suspected involvement in malware-enabled scams…
Jun 18, 2024NewsroomVulnerability / Cryptojacking Cybersecurity researchers have uncovered a new malware campaign that targets publicly exposed Docket API endpoints…
Threat Actors (TAs) associated with the notorious MEDUSA ransomware have escalated their activities and have allegedly targeted two institutions in…
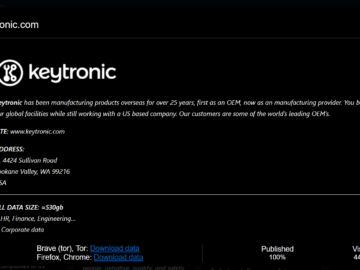
Keytronic confirms data breach after ransomware attack Pierluigi Paganini June 18, 2024 Printed circuit board assembly (PCBA) manufacturer Keytronic disclosed…
Hackers use social engineering as it focuses on the psychological rather than technological aspects of security flaws, consequently easily tricking…
VMware by Broadcom has fixed two critical vulnerabilities (CVE-2024-37079, CVE-2024-37080) affecting VMware vCenter Server and products that contain it: vSphere…
Jun 18, 2024NewsroomMobile Security / Financial Fraud The Singapore Police Force (SPF) has announced the extradition of two men from…
Guidehouse Inc., based in McLean, Virginia, and Nan McKay and Associates, headquartered in El Cajon, California, have agreed to pay…
A recently identified ransomware variant dubbed OPIX encrypts user files using a random character string and adds the “.OPIX” extension…
On June 13, 2024, the Cybersecurity and Infrastructure Security Agency (CISA) made history by conducting the federal government’s inaugural tabletop…
Software security requires a creative and disciplined approach. It involves having the vision to develop secure strategy, tactics, and execution….
Jun 18, 2024NewsroomNetwork Security / Vulnerability VMware has released updates to address critical flaws impacting Cloud Foundation, vCenter Server, and…