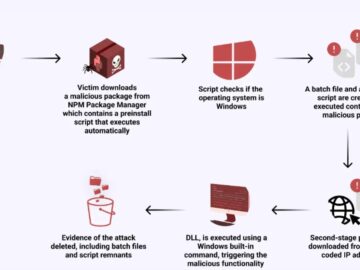
In December 2023, we reported on how North Korean threat actors, particularly Jade Sleet, have been compromising supply chains through…
Jun 14, 2024NewsroomDevice Security / Authentication An analysis of a hybrid biometric access system from Chinese manufacturer ZKTeco has uncovered…
Former subpostmasters and Post Office branch staff who were wrongfully convicted of crimes based on flawed computer evidence in Scotland…
Hacktivist group 177 Members Team has claimed a cyberattack on Malaysia’s leading internet service provider, Unifi TV. The Unifi TV…
Ascension, a leading healthcare provider, has made significant strides in its investigation and recovery efforts following a recent cybersecurity breach….
The U.S. food chain giant Panera Bread has begun notifying its employees of a significant data breach that occurred as…
Life360, a company known for its family safety services, recently fell victim to a criminal extortion attempt. The company received…
Microsoft publicly disclosed several months ago that a Chinese hacking group, Storm-0558, breached its servers in early the previous year,…
Threat actors linked to North Korea have accounted for one-third of all the phishing activity targeting Brazil since 2020, as…
Dordt University, a distinguished private Christian liberal arts college renowned for its reformed Christian perspective on education, has encountered a…
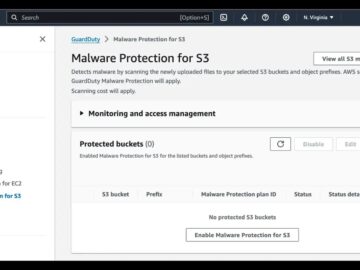
Amazon Web Services (AWS) has announced the general availability of Amazon GuardDuty Malware Protection for Amazon Simple Storage Service (Amazon…
In the ever-evolving landscape of cybersecurity, staying ahead of threats is paramount. One crucial tool in the arsenal of cybersecurity…