Cybersecurity watchdog Shadowserver has identified 256,000+ publicly exposed servers vulnerable to a critical Remote Code Execution (RCE) flaw in Microsoft…
Fortinet has disclosed multiple stack-based buffer overflow vulnerabilities (CVE-2024-23110) in FortiOS’s command line interpreter. These vulnerabilities could allow authenticated attackers…
Ascension, which fell victim to a ransomware attack in the initial week of May, swiftly initiated an investigation to address…
In this Help Net Security interview, Mark Nelsen, SVP and Global Head of Consumer Product at Visa, discusses the integration…
Ukrainian cyber police have arrested a 28-year-old man from Kyiv, identified as a key figure in the development of cryptors…
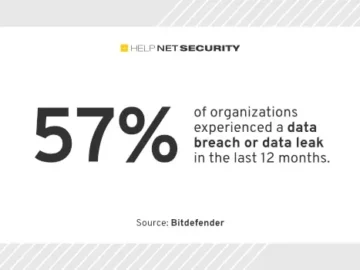
“Businesses across every industry face unprecedented challenges posed by an increasing attack surface, zero-day vulnerabilities, cloud misconfigurations, and new emerging…
Planning on launching Copilot? Here’s how to make your flight smoother. AI has been heralded for its game changing potential….
Spending on public cloud services continues to rise unabated, with end-user spending set to top $1T in 2027. But with…
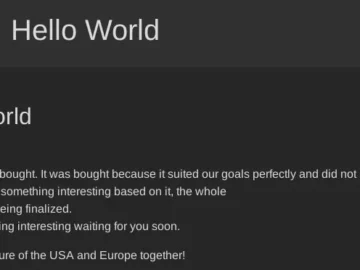
The notorious Monti ransomware has been sold to new owners. According to the actor’s latest update, “This project was bought….
A new phishing campaign uses HTML attachments that abuse the Windows search protocol (search-ms URI) to push batch files hosted on…
CISA adds Arm Mali GPU Kernel Driver, PHP bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini June 12, 2024…
The second Jira website I discovered was surprisingly harder to exploit. It didn’t give me the verbose errors like the…