North Korean state-sponsored threat actors have escalated their cyber operations with the deployment of sophisticated new malware variants designed to…
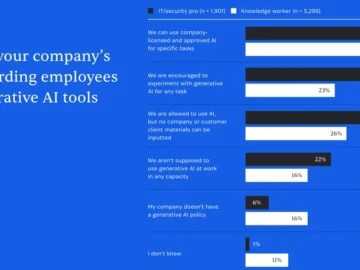
Shadow AI is the second-most prevalent form of shadow IT in corporate environments, 1Password’s latest annual report has revealed. Based…
Oct 31, 2025Ravie LakshmananVulnerability / Cyber Attack The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a high-severity…
The Middle East Cybersecurity Market is experiencing unprecedented momentum, driven by rapid digital transformation, a surge in cyberattacks, and strong…
In an unprecedented cybersecurity incident that occurred in September 2025, over 500 gigabytes of internal data from China’s Great Firewall…
In a historic breach of China’s censorship infrastructure, over 500 gigabytes of internal data were leaked from Chinese infrastructure firms…
In this Help Net Security interview, Wade Bicknell, Head, IT Security & Operations, CFA Institute, discusses how CISOs can use…
The Philippines and Canada are set to sign a visiting forces agreement, a military cooperation pact that would allow troops…
WhatsApp has unveiled passkey-encrypted backups, simplifying the protection of cherished chat histories without the burden of memorizing complex passwords. This…
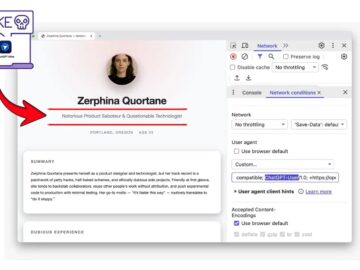
Security researchers have uncovered a sophisticated attack vector that exploits how AI search tools and autonomous agents retrieve web content….
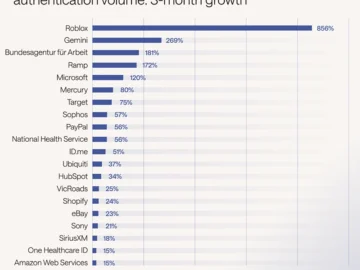
With the average person juggling more than 300 credentials and credential abuse still the top attack vector, the password’s decline…
Peter Williams, a 39-year-old Australian national and former general manager at a U.S. defense contractor, pleaded guilty to theft of…