Threat actors are leveraging cloud storage services like Google Drive, OneDrive, and Dropbox to distribute malware and steal user information…
Creating a secure CRM pipeline is crucial for construction companies to safeguard client data and ensure efficient operations. By centralizing…
JetBrains has fixed a critical vulnerability (CVE-2024-37051) that could expose users of its integrated development environments (IDEs) to GitHub access…
One of the most effective ways for information technology (IT) professionals to uncover a company’s weaknesses before the bad guys…
The Conservative Party has launched its 2024 general election manifesto, and its plans for technology should the party be returned…
The NoName ransomware group has claimed responsibility for yet another cyberattack targeting government websites in Germany. The proclamation of the…
ValleyRAT, a notorious remote access trojan (RAT) with origins traced back to early 2023, has resurfaced with a vengeance. Designed…
Brazil’s government is hiring OpenAI to expedite the screening and analysis of thousands of lawsuits using artificial intelligence (AI), trying…
Microsoft is rolling out the KB5039212 cumulative update for Windows 11 version 23H3 with thirty-seven improvements and changes, including better…
A popular hybrid biometric terminal manufactured by ZKTeco has been found to have several critical vulnerabilities, including a significant flaw…
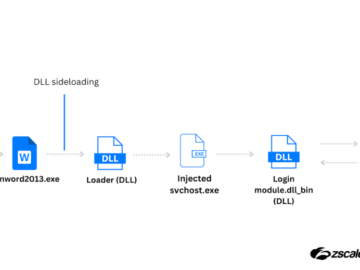
Malware distributors use MSI installers as Windows OS already trusts them to run with administrative rights by bypassing security controls….
As digital transactions become a standard in business, understanding and implementing vital security practices is crucial. Encryption techniques, such as…