Tenable Holdings has officially announced its acquisition of Eureka Security Inc, although the financial details remain undisclosed. Eureka Security Inc,…
11 Jun 25 Fastest Growing Cybersecurity Companies Posted at 08:54h in Blogs by Di Freeze This week in cybersecurity from…
June 2024 Patch Tuesday is here and Microsoft has delivered fixes for a critical MSMQ flaw (CVE-2024-30080) and a RCE…
The British and Canadian privacy authorities have announced they will undertake a joint investigation into the data breach at global…
Jun 11, 2024The Hacker NewsEndpoint Security / Incident Response Managed service providers (MSPs) are on the front lines of soaring…
As with most endeavours, incorporating security into the process as early as possible is essential when building or migrating to…
Researchers have discovered a new phishing campaign in which threat actors distribute the Remcos RAT malware within UUEncoding (UUE) file…
In a bold attempt to redefine cloud security and privacy standards, Apple has unveiled Private Cloud Compute (PCC), a groundbreaking…
WA Police will specifically recognise teams working on technology projects for the first time in its annual recognition of excellence…
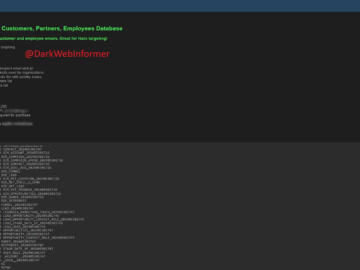
Cylance confirms the legitimacy of data offered for sale in the dark web Pierluigi Paganini June 11, 2024 A threat…
We’ve recently announced a new Domains page and major improvements to existing capabilities for setting custom attack surface policies. These…
Microsoft has released the Windows Server 2022 KB5039227 and Windows Server 2019 KB5039217 cumulative updates with security fixes and fixes…