Peter Williams, a 39-year-old Australian national and former general manager at a U.S. defense contractor, pleaded guilty to theft of…
The Cybersecurity and Infrastructure Security Agency (CISA), working alongside the National Security Agency and international cybersecurity partners, has released a…
Here’s a look at the most interesting products from the past month, featuring releases from: Acronis, Akeyless, Axoflow, Blumira, Cayosoft,…
Suncorp has commenced “full-scale delivery” of agentic AI into its operations, predicting it will allow the insurer to “completely re-imagine”…
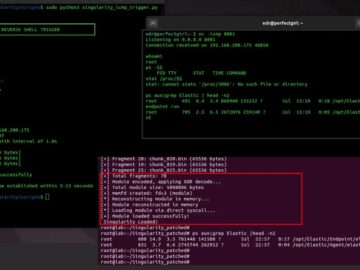
A sophisticated Linux kernel rootkit designed to slip past the defenses of Elastic Security, a leading endpoint detection and response…
Oct 31, 2025The Hacker NewsEndpoint Security / Network Security A design firm is editing a new campaign video on a…
Ever since Anthropic released Skills I’ve been thinking about how to optimize my Personal AI Infrastructure using the proper hierarchy….
The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2025-41244 to its Known Exploited Vulnerabilities catalog. This local privilege escalation…
The Cybersecurity and Infrastructure Security Agency and the National Security Agency on Thursday unveiled a best-practices guide to help organizations…
A new security-focused AI model released Thursday by OpenAI aims to automate bug hunting, patching and remediation. The model, powered…
U.S. CISA adds XWiki Platform, and Broadcom VMware Aria Operations and VMware Tools flaws to its Known Exploited Vulnerabilities catalog…
The Akira ransomware group claims to have breached Apache OpenOffice and stolen 23GB of data. Apache OpenOffice, for those unfamiliar,…