What Is a Vulnerability Disclosure Program? A VDP is a structured method for anyone to report vulnerabilities. VDPs should include…
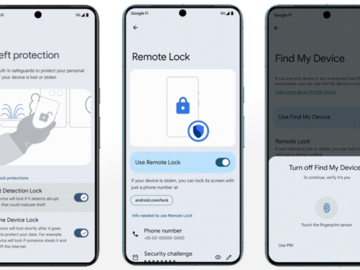
Google is introducing multiple anti-theft and data protection features later this year, some available only for Android 15+ devices, while…
May 15, 2024NewsroomPrivacy / Data Protection Google has announced a slew of privacy and security features in Android, including a…
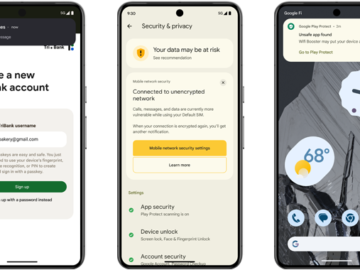
Today, Google announced new security features coming to Android 15 and Google Play that will help block scams, fraud, and malware apps…
May 15, 2024NewsroomData Breach / Cyber Crime Law enforcement agencies have officially seized control of the notorious BreachForums platform, an…
An international law enforcement operation led by the United States’ Federal Bureau of Investigation (FBI), with assistance from the UK’s…
Mastering text preprocessing to send more input to ChatGPT. In order for chatbots and voice assistants to be helpful, they…
A Tornado Cash developer has been sentenced to 64 months in prison Pierluigi Paganini May 15, 2024 One of the…
As a recipient of HackerOne’s prestigious 2024 ‘Win as a Team’ award, I’m excited to share my thoughts on what…
The U.S. Department of Justice has indicted two brothers for allegedly manipulating the Ethereum blockchain and stealing $25 million worth…
May 15, 2024NewsroomAndroid Security / Malware Google is unveiling a set of new features in Android 15 to prevent malicious…
Political candidates, election officials and others at high risk of being targeted online are being offered protection against phishing and…