The notorious data leak site BreachForums has been taken over by the police. Cybercrime and data leaks are still being…
Nissan says that the personal information of more than 53,000 workers has been stolen. The huge automaker is now taking…
Google is gearing up to introduce a groundbreaking feature aimed at enhancing smartphone security through the power of Artificial Intelligence…
Cloud security incidents are alarmingly on the rise, with 61% of organizations reporting breaches within the last year, marking a…
NBN Co will fast-track industry discussions about multi-gigabit services, proposing three new 2Gbps products for home and business users in…
Three vulnerabilities associated with CSS injection, file upload, and remote code execution have been discovered in the SAP Customer Experience…
Two critical vulnerabilities have been discovered in D-Link DIR-X4860 routers which were associated with Authentication bypass due to HNAP port…
Historically, the utility industry has been thought of as reliable, slow moving, and heavily regulated. People want to know that…
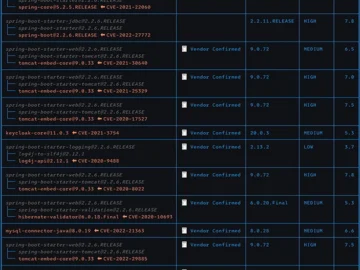
OWASP dep-scan is an open-source security and risk assessment tool that leverages information on vulnerabilities, advisories, and licensing restrictions for…
Following the massive Nissan data breach from November last year that exposed the Social Security numbers of thousands of former…
CSIRO is on the hunt for a chief information security officer to fill a role vacated over two years ago….
Cybereason, the leader in future-ready attack protection, today announced the availability of Cybereason Mobile Threat Defense, powered by Zimperium. This…