Google has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence…
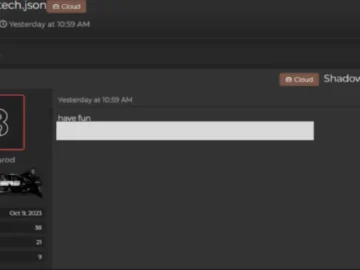
A dark web actor named “komarod” is claiming credit for a June 8 Shadow PC data breach, allegedly stealing data…
Apple is set to make a significant announcement at the Worldwide Developers Conference (WWDC), which kicks off on June 10. According to Bloomberg’s Mark Gurman, the tech giant will introduce…
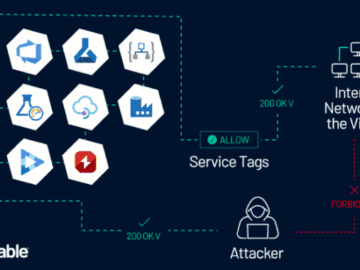
Jun 10, 2024NewsroomCloud Security / Vulnerability Microsoft is warning about the potential abuse of Azure Service Tags by malicious actors…
SAP talked a lot about artificial intelligence (AI) and generative AI at its annual Sapphire customer event in Orlando last…
By Joe Guerra, M.Ed, CASP+, Professor of Cybersecurity, Hallmark University When we talk about the cloud, it’s not just a…
Electronic health records (EHRs) have become crucial tools for storing and managing patient information. These digital records contain a wealth…
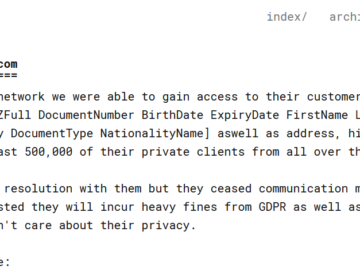
LendingTree subsidiary QuoteWizard and automotive parts provider Advance Auto Parts have been revealed as victims of attackers who are trying…
Staying Sharp: Cybersecurity CPEs Explained Perhaps even more so than in other professional domains, cybersecurity professionals constantly face new threats….
Subpostmasters used pre-Horizon Capture software without any training from the Post Office, a failing that mirrors one of the causes…
The wait is finally over! The Cyber Express is thrilled to announce the much-anticipated return of World CyberCon, India Edition….
Christie’s data breach impacted 45,798 individuals Pierluigi Paganini June 10, 2024 Auction house Christie’s revealed that the data breach caused by…