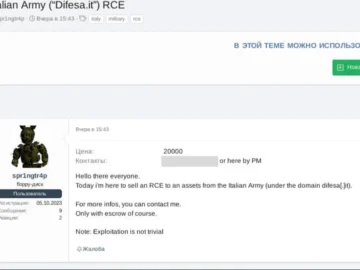
A threat actor known as spr1ngtr4p has purportedly advertised a Remote Code Execution (RCE) vulnerability affecting a subdomain of Italy’s…
Generative artificial intelligence (GenAI) is reshaping our world, from streamlining work tasks like coding to helping us plan summer vacations….
DuckDuckGo has unveiled a new feature, AI Chat, which offers users an anonymous way to access popular AI chatbots. This…
Sophos, a global leader in innovative security solutions designed to combat cyberattacks, has announced the appointment of Joe Levy as…
A threat actor known as Desec0x has claimed to possess a database allegedly stolen from the State Grid Corporation of…
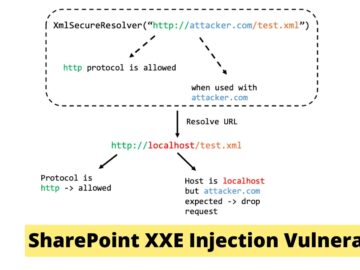
A new XXE (XML eXternal Entity) Injection has been discovered to affect SharePoint on both on-prem and cloud instances. This…
June 7, 2024 – Google has announced it will delete Location History (Timeline) data and store new data locally, starting…
Frontier Communications Parent, Inc. (the “Company”) detected unauthorized access to portions of its information technology environment. The breach, attributed to…
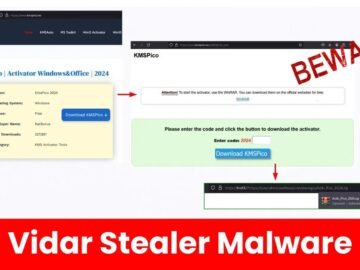
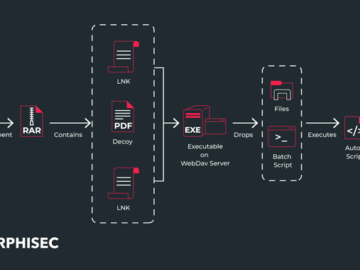
Researchers detected an attack involving a fake KMSPico activator tool, which delivered Vidar Stealer through several events. The attack leveraged…
Every time a new version of the Windows operating system (OS) is released, the countdown clock starts ticking on the…
Jun 10, 2024NewsroomCyber Espionage / Malware Cybersecurity researchers have disclosed details of a threat actor known as Sticky Werewolf that…
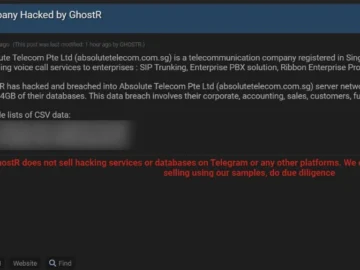
Absolute Telecom Pte Ltd, a prominent telecommunications company based in Singapore, has fallen victim to an alleged cyberattack. The Absolute…