The Computer Emergency Response Team of Ukraine (CERT-UA) reports about a new campaign dubbed “SickSync,” launched by the UAC-0020 (Vermin)…
Amid the ongoing elections for the European Parliament, the Russia-aligned NoName057(16) cyber criminal operation says it is launching extensive distributed…
A new PHP for Windows remote code execution (RCE) vulnerability has been disclosed, impacting all releases since version 5.x, potentially…
ARC Labs delved into the intricacies of the Wineloader backdoor, a sophisticated tool used in spearphishing campaigns linked to the…
The North Korean state-sponsored group known as Kimsuky has launched a sophisticated cyber-espionage campaign targeting a prominent weapons manufacturer in…
Salesforce has unveiled its UK artificial intelligence (AI) centre, located in London’s Blue Fin building, which officially opens on June…
The University of Arkansas is spearheading a new collaborative effort with researchers and industry partners to address the rising risks…
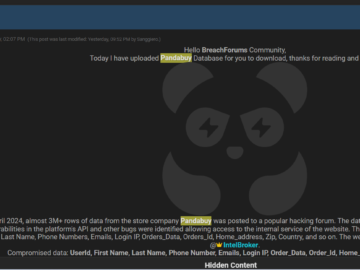
Pandabuy was extorted twice by the same threat actor Pierluigi Paganini June 07, 2024 Chinese shopping platform Pandabuy previously paid…
Microsoft’s Windows Recall is a new feature for Copilot+ PCs, announced in May 2024. It takes periodic screenshots (every 5…
Hacktivist groups are increasingly targeting critical infrastructure’s Operational Technology (OT) systems, motivated by geopolitical issues that, unlike traditional website defacements,…
How Interactive Sandboxing Can Benefit Your Organization By Vlad Ananin, Technical Writer at Any.Run The current rate and complexity of…
With summer in full swing, most seasonal businesses are well underway. From landscape maintenance to pool care to summer rentals…