07 Jun Getting More Women Into Cybersecurity Amid The Cyber Skills Gap Posted at 09:10h in Blogs by Di Freeze…
The Dutch Authority for the Financial Markets (AFM) and the monetary authority, De Nederlandsche Bank (DNB), are in the midst…
A threat actor has come forward, asserting responsibility for a significant breach in the security infrastructure of HopSkipDrive, a well-known…
Hackers can hide their names and access blocked websites or networks by using proxy servers, which help make these systems…
Apache RocketMQ platform is a widely used messaging system that handles high volumes of data and critical operations, often attracting…
A security vulnerability in Ariane Allegro Hotel Check-In Kiosks exposed guest data and potentially compromised room access. However, a patch…
Insider threats are a growing concern for organizations of all sizes and industries, and can be both intentional and unintentional,…
In an interview with Computer Weekly, Gaia-X CEO Ulrich Ahle admitted that stubborn international differences in law and technology standards…
Threat actors are constantly evolving their TTPs and developing new malicious tools to execute their activities. Recently, Akamai researchers have…
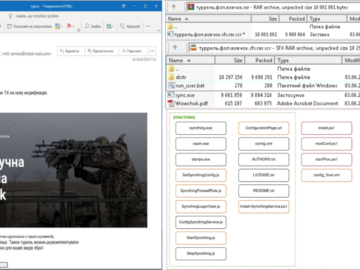
UAC-0020 threat actor used the SPECTR Malware to target Ukraine’s defense forces Pierluigi Paganini June 07, 2024 Ukraine CERT-UA warned…
The widely used PHP programming language has been discovered with a new remote code execution vulnerability deemed critical severity. Further,…
The government computer emergency response team of Ukraine, CERT-UA, in direct cooperation with the Cyber Security Center of the Armed…