Tenable® Holdings, Inc., a leading Exposure Management company, has announced a definitive agreement to acquire Eureka Security, Inc., a prominent…
Apple Inc is gearing up to introduce its own password management application at the upcoming Worldwide Developer Conference, aiming to…
The CyRC Vulnerability Advisory has reported a critical security flaw in EmailGPT, an AI-powered email writing assistant and Google Chrome…
It is difficult to secure cloud accounts from threat actors who exploit multi-factor authentication (MFA) settings. Threat actors usually alter…
In an era where digital dominance reigns supreme, tech giants like Google stand as pillars of innovation and progress. However,…
Ransomware remains an ongoing threat for organizations and is the largest single cause of IT outages and downtime as 41%…
Jun 07, 2024NewsroomCryptojacking / Vulnerability The threat actor known as Commando Cat has been linked to an ongoing cryptojacking attack…
On June 6, 2024, a cyberattack on UAE Ministry of Education’s website was claimed by a dark web actor. The…
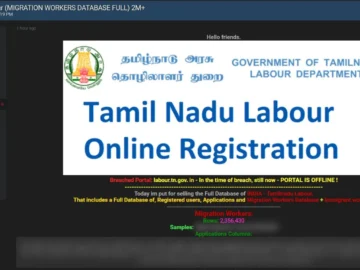
A massive data breach has allegedly been reported in the Indian state of Tamil Nadu, where apparently data of over…
May 2024 Patch Tuesday was unusual because we had security updates from Adobe, Apple, Google, Mozilla, and Microsoft on the…
Here’s a look at the most interesting products from the past week, featuring releases from Appdome, SailPoint, Tines, Trend Micro,…
26% of organizations don’t provide IT security training to end-users, according to Hornetsecurity. The Hornetsecurity survey, which compiled feedback from…