Early in 2024, Wing Security released its State of SaaS Security report, offering surprising insights into emerging threats and best…
By Neelesh Kripalani, Chief Technology Officer, Clover Infotech Generative AI, which includes technologies such as deep learning, natural language processing,…
Security researchers analyzing the relatively new RansomHub ransomware-as-a-service believe that it has evoloved from the currently defunct Knight ransomware project. RansomHub has a…
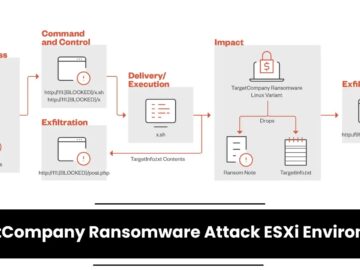
The notorious TargetCompany ransomware group introduced a new Linux variant targeting VMware ESXi environments. This evolution in their tactics underscores…
Phishing attackers are distributing malicious HTML files as email attachments, containing code designed to exploit users by prompting them to…
HyperCycle enhances AI safety and efficiency with cryptographic proofs and peer-to-peer nodes. HyperShare supports decentralized governance and income distribution, promoting…
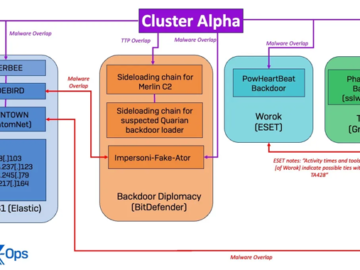
Jun 05, 2024NewsroomCyber Espionage / Threat Intelligence An unnamed high-profile government organization in Southeast Asia emerged as the target of…
The FBI is warning about a surge in work-from-home scams preying on individuals seeking legitimate employment opportunities. These scams often…
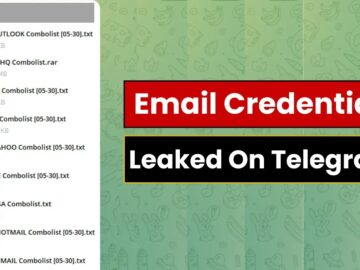
Last week, a security researcher sent me 122GB of data scraped out of thousands of Telegram channels. It contained 1.7k…
An analysis of a nascent ransomware strain called RansomHub has revealed it to be an updated and rebranded version of…
Research looking into IT project management has found almost two-thirds of projects that use the Agile Manifesto fail. The research,…
Less than a week after The Cyber Express exposed the data breach of a crime reporting app in India’s Telangana…