There is a healthy relationship between large language models (LLMs) and graph databases, which are used to draw in information…
CrowdStrike and NinjaOne, a frontrunner in IT platform services for endpoint management, security, and visibility, have announced a strategic partnership….
Enterprises are being targeted by the malware known as SocGholish through deceptive browser update prompts. This malware, notorious for its…
In today’s world, cybersecurity is a worry for businesses across various sectors. As technology progresses, cybercriminals also refine their strategies….
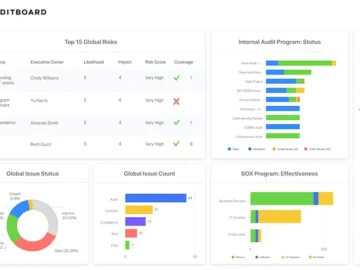
AuditBoard announced powerful enhancements for its InfoSec Solutions to help organizations meet their IT compliance, cyber risk, and vendor risk…
Medical health care provider DocGo has disclosed in a form 8-K that it experienced a cybersecurity incident involving some of…
Social media firms must implement effective age-checks and “tame toxic algorithms” recommending harmful content to children, according to Ofcom’s new…
The TXT files often contain sensitive information like passwords, configuration details, or system logs, due to which it attracts hackers….
The US Cybersecurity and Infrastructure Agency (CISA) has announced the creation of “Vulnrichment,” a new project that aims to fill…
Ascension, one of the largest nonprofit healthcare systems in the United States, is facing disruptions in clinical operations due to…
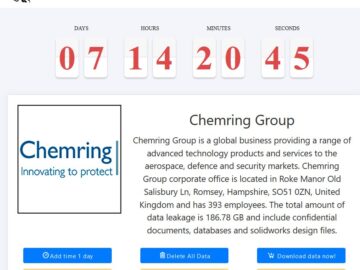
The Medusa ransomware group has demanded $3.5 million from the Chemring Group on their leak site, along with a looming…
Brandywine Realty Trust, a significant U.S. real estate investment trust, has confirmed a disruption to its operations due to a…