On its help pages, OpenAI says ChatGPT web users without accounts should navigate to Settings and then uncheck Improve the…
On April Patch Tuesday, Microsoft fixed 149 bugs—one of the biggest security update releases in the company’s history. Many of…
Apr 10, 2024NewsroomHardware Security / Linux Cybersecurity researchers have disclosed what they say is the “first native Spectre v2 exploit”…
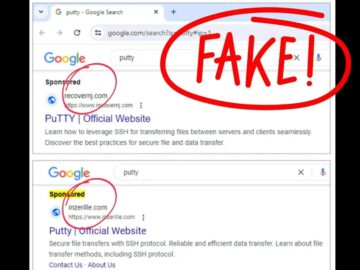
A sophisticated malvertising campaign is targeting system administrators across North America. The attackers are using fake ads for popular system utilities to distribute a dangerous…
The Change Healthcare ransomware attack has taken a third cruel twist. A new ransomware group, RansomHub, has listed the organisation…
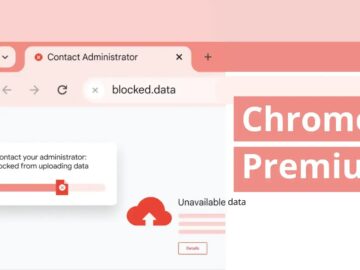
Google has unveiled a significant upgrade to its enterprise browsing capabilities with the launch of Chrome Enterprise Premium. This new…
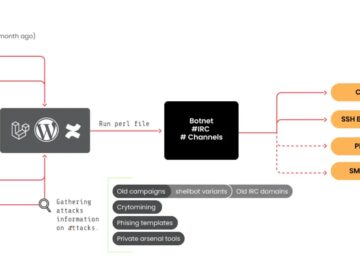
The cybersecurity community is again on high alert as the notorious botnet group RUBYCARP, known for its SSH brute force…
Apr 10, 2024The Hacker NewsWebinar / Identity Security We all know passwords and firewalls are important, but what about the…
Multiple vulnerabilities have been discovered in FortiOS and FortiProxy that were related to administrator cookie leakage, arbitrary command execution and…
A new critical vulnerability has been discovered in two of the Rust standard libraries, which could allow a threat actor…
The UK needs to build on its relationship with South Korea to improve its semiconductor supply chain resiliency. This is among…
Cybersecurity in the Evolving Threat Landscape Pierluigi Paganini April 10, 2024 As technology evolves and our dependence on digital systems…