German remote access software provider TeamViewer has revealed details of an initiative called SheSportTech that aims to help “women explore…
Image: Midjourney A Romanian botnet group named ‘RUBYCARP’ is leveraging known vulnerabilities and performing brute force attacks to breach corporate…
Paris Saint-Germain (PSG), one of France’s premier football clubs, has been the victim of a cyber attack. The club’s ticketing…
Today, Keeper Security have announced the introduction of Time-Limited Access and Self-Destructing Records, boosting secure access management for businesses. These…
Ahoy, which is often associated with communicating to ships, has now been playfully adopted in pirate language. We coin ‘Ahoi,’…
Google has recently announced a significant upgrade to its Workspace platform, integrating cutting-edge Artificial Intelligence (AI) technology to enhance meetings…
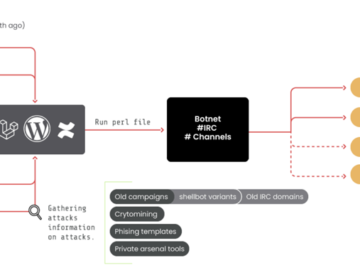
Apr 09, 2024NewsroomBotnet / Crypto Mining A threat group of suspected Romanian origin called RUBYCARP has been observed maintaining a…
The outbreak of war in Ukraine in February 2022 marked the dawning of a long-predicted era in which cyber space…
This year, Crowdfense is expanding its scope to encompass additional major research fields like Enterprise Software, WiFi/Baseband, and Messengers and…
By Rishi Baviskar, Global Head of Cyber Risk Consulting at Allianz Commercial Improvements in cyber security and business continuity are…
Synopsys has introduced Black Duck® Supply Chain Edition, a novel software composition analysis (SCA) solution. This offering aids organisations in…
Hackers exploit Oracle WebLogic Servers, knowing that they are extensively used in enterprises. Threat actors can use security vulnerabilities present…