Police forces are checking intelligence and criminal databases following warnings of errors in data supplied to police and intelligence services…
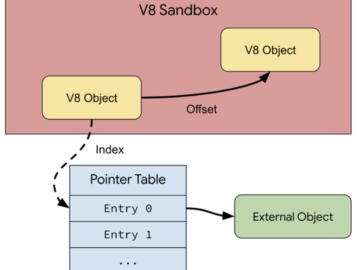
Google announces V8 Sandbox to protect Chrome users Pierluigi Paganini April 09, 2024 Google announced support for a V8 Sandbox in the…
Threat actors have been discovered exploiting a Fortinet Forticlient EMS vulnerability to install unauthorized RMM tools and PowerShell backdoors on…
In a recent announcement, the team behind the widely acclaimed source code editor, Notepad++, has issued a call to arms…
Greece’s Ministry of Migration and Asylum has received a significant €175,000 fine for violating data and privacy protection regulations in…
Hackers always end up targeting famous YouTube channels because of their large audience base, and their aim is to exploit…
Privacy mistakes could pose a serious threat to sensitive information or systems,, which threat actors could exploit for their gain….
Apr 09, 2024NewsroomMalware / Cryptojacking Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver…
A recent lawsuit was filed by Google against two app developers, Yunfeng Sun (also known as Alphonse Sun) and Hongnam…
Google has announced the global rollout of its revamped Find My Device network. This innovative feature is set to transform…
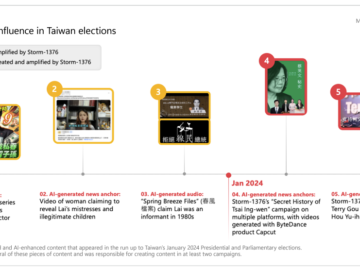
China is using generative AI to carry out influence operations Pierluigi Paganini April 09, 2024 China-linked threat actors are using…
Researchers identified a significant vulnerability within the HTTP/2 protocol, potentially allowing hackers to launch Denial of Service (DOS) attacks on…