Confluent has released Confluent Private Cloud, the simplest way to deploy, manage, and govern streaming data on private infrastructure. The…
Canadian authorities have issued an urgent alert following multiple confirmed incidents where cybercriminals compromised internet-accessible Industrial Control Systems (ICS) devices…
A sophisticated malware campaign is actively targeting WordPress e-commerce websites using the WooCommerce plugin, according to recent findings from the…
SUSE has released SUSE Linux Enterprise Server (SLES) 16, calling it AI-ready and built for long-term use. The release marks…
Fujitsu grew its UK public sector business over the last 12 months despite widespread criticism for its role in the…
The VSCode extension marketplace has become a critical vulnerability in the software supply chain. Security researchers at HelixGuard Team recently…
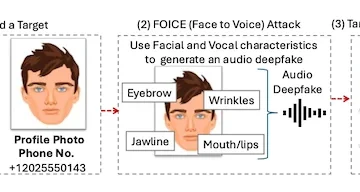
A photo of someone’s face may be all an attacker needs to create a convincing synthetic voice. A new study…
A critical security flaw has been discovered in the Anti-Malware Security and Brute-Force Firewall WordPress plugin, putting more than 100,000…
Even with strong wireless encryption, privacy in connected homes may be thinner than expected. A new study from Leipzig University…
Manish Mimami, founder and CEO of Protectt.ai For years, static passwords, dynamic One-time Passwords (OTPs), and Multi-factor Authentication (MFA) have…
The United States Department of Justice said Peter Williams, an Australian who worked as the general manager for a division…
Google has officially promoted Chrome 142 to the stable channel, delivering critical security updates for Windows, Mac, and Linux users….