In March 2024, MarineMax, a prominent yacht retailer in Florida, USA, confirmed a cybersecurity incident. It fell victim to a…
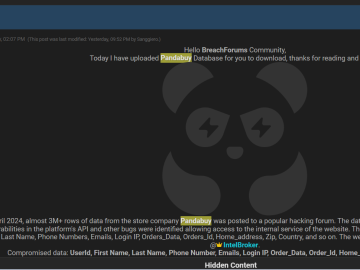
PandaBuy data breach allegedly impacted over 1.3 million customers Pierluigi Paganini April 02, 2024 Threat actors claimed the hack of…
Octopus Server, a popular automation tool for deployment, operations runbooks, and development tasks, has identified a critical security flaw. The…
On Friday, a lone Microsoft developer rocked the world when he revealed a backdoor had been intentionally planted in XZ…
A critical vulnerability has been identified in the xz-utils package, versions 5.6.0 to 5.6.1, which harbors a backdoor capable of…
Apr 02, 2024NewsroomBrowser Security / Data Security Google has agreed to purge billions of data records reflecting users’ browsing activities…
The cybersecurity landscape faces a new threat with the emergence of ‘darcula,’ a Phishing-as-a-Service (PhaaS) platform. This sophisticated service enables…
Veracode, a leading provider in the cybersecurity space, has officially announced its acquisition of Longbow Security. This strategic move is…
A critical vulnerability has been discovered within the XZ Utils library (a command line tool for compressing and decompressing XZ…
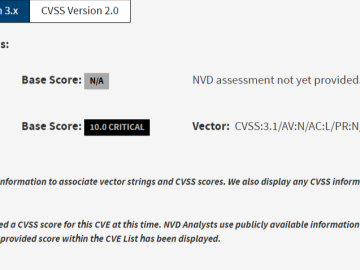
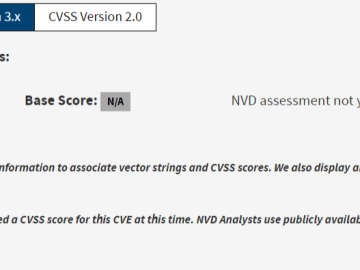
A critical security flaw, identified as CVE-2023-50969, has recently been discovered in Imperva SecureSphere, a popular on-premise Web Application Firewall…
A backdoor was recently discovered in the xz-utils package versions 5.6.0 to 5.6.1, shocking the Linux community. This poses a…
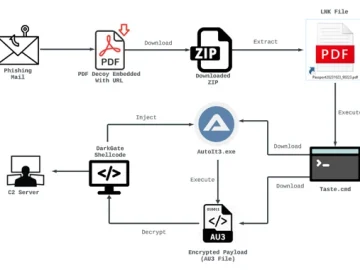
Apr 02, 2024NewsroomMalvertising / Threat Intelligence The threat actor known as TA558 has been attributed to a new massive phishing…