In 2023, C2A Security added multiple OEMs and Tier 1s to its portfolio of customers, successful evaluations, and partnerships such…
PyPI hit by malware attack! Malicious packages targeting crypto wallets & browser data. Platform suspends new users & projects. Learn…
The UK’s HM Treasury has expanded its headcount of data scientists as part of its plans to drive “data transformation”…
If your job involves keeping applications or data secure, you know how important penetration testing can be in identifying potential…
C2A Security’s DevSecOps Platform, ‘EVSec’, has been gaining widespread traction as the automotive industry rushes to meet cybersecurity regulations and…
In a concerning development, a well-known ransomware collective known as INC Ransom has recently disclosed a portion of pilfered data…
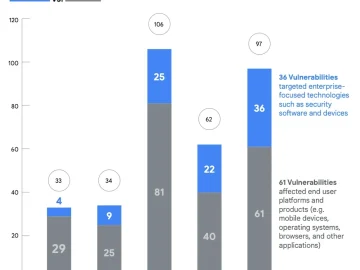
2023 saw attackers increasingly focusing on the discovery and exploitation of zero-day vulnerabilities in third-party libraries (libvpx, ImagelO) and drivers…
Social media giant Facebook snooped on Snapchat users’ network traffic, engaged in anticompetitive behavior and exploited user data through deceptive…
A sophisticated phishing-as-a-service (PhaaS) platform called Darcula has set its sights on organizations in over 100 countries by leveraging a…
Sellafield Ltd, the Nuclear Decommissioning Authority-backed organisation currently working to wind up operations at the troubled Sellafield nuclear facility in…
Hackers have been found leveraging weaponized virtual hard disk (VHD) files to deploy the notorious Remote Control Software (RAT), Remcos….
Zoom has taken a monumental leap forward by introducing Zoom Workplace, an all-encompassing AI-powered platform designed to redefine how we…