[Pieter Danhieux Co-Founder and CEO, Secure Code Warrior] The doomsayers are, so far, losing the argument. The panic around AI…
NHS Dumfries and Galloway (part of NHS Scotland) has confirmed that a “recognised ransomware group” was able to “access a…
Mar 28, 2024NewsroomHardware Security / Vulnerability Cybersecurity researchers from ETH Zurich have developed a new variant of the RowHammer DRAM…
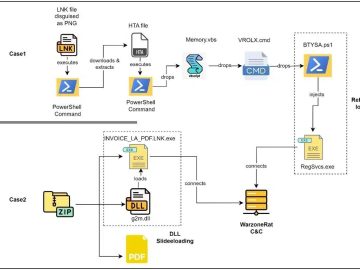
WarzoneRAT, the notorious Remote Administration Tool (RAT) malware, made a comeback despite the FBI’s efforts to dismantle its operations earlier…
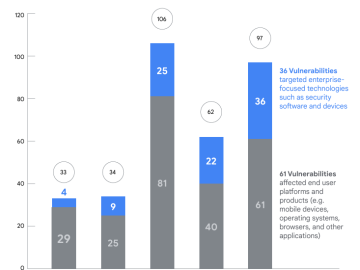
Google: China dominates government exploitation of zero-day vulnerabilities in 2023 Pierluigi Paganini March 28, 2024 Google’s Threat Analysis Group (TAG)…
Coro, the leading cybersecurity platform purpose-built for small and medium-sized enterprises (SMEs), today announced it has secured $100 million in…
Google has released an update to Chrome which includes seven security fixes. Version 123.0.6312.86/.87 of Chrome for Windows and Mac…
Mar 28, 2024The Hacker NewsSecrets Management / Zero Trust In the whirlwind of modern software development, teams race against time,…
Little is known publicly about Epstein’s activities in the decade prior to his 2019 arrest. The majority of women who…
Black Lotus Labs discovered a multi-year campaign by TheMoon malware targeting vulnerable routers and turning them into bots for the…
In this podcast, we look at distributed cloud storage with Enrico Signoretti, vice-president of product and partnerships at Cubbit. We…
A new threat has emerged, targeting unsuspecting iPhone users through the seemingly secure iMefofferssage platform. A sophisticated Phishing-as-a-Service (PhaaS) platform…