In an increasingly digitized world, the threat of cyber attacks looms large over businesses, governments, and individuals alike. Among the…
The First American Financial Corporation, one of the largest title insurance companies in the United States, revealed that a cyberattack…
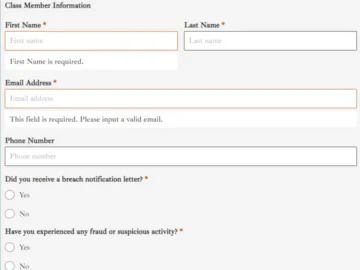
TRC Staffing is at the center of a concerning data breach, leaving personal information vulnerable to cybercriminals. Murphy Law Firm…
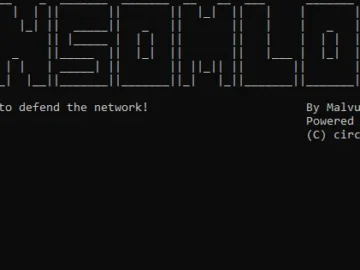
RansomLord is an open-source tool that automates the creation of PE files, which are used to exploit ransomware pre-encryption. “I…
Cyber risk management has many components. Those who do it well will conduct comprehensive risk assessments, enact well-documented and well-communicated…
Cloud Security Engineer – Secret Clearance Required Constellation West | USA | Remote – View job details As a Cloud…
This article includes excerpts from various reports that provide statistics and insights on GenAI and its impact on businesses. CEOs…
ShinyHunters hacking group has claimed to have breached Ticketmaster, stealing the personal data of 560 million users. The 1.3 TB…
A parliamentary submission published online had to be withdrawn after it was found to contain false information about a third-party…
First American Financial Corporation, the second-largest title insurance company in the United States, revealed Tuesday that a December cyberattack led…
Fintech firm Klarna said it is using AI for purposes such as running marketing campaigns and generating images, saving about…
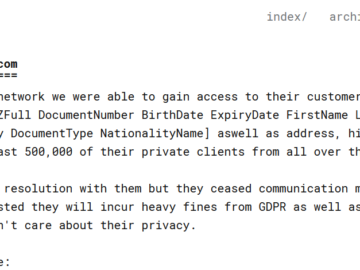
Christie disclosed a data breach after a RansomHub attack Pierluigi Paganini May 28, 2024 Auction house Christie disclosed a data breach…