The Metropolitan Police has confirmed it is setting up a national investigation into the Post Office scandal, although it could…
The impact of the Cencora data breach is far more widespread than earlier thought as more than a dozen pharmaceutical…
A recent data breach has reportedly compromised the personal information of Decathlon employees in Spain. The threat actor known as…
A new privilege escalation vulnerability has been discovered in Zscaler Client Connector, combining three different vulnerabilities. The three vulnerabilities were…
A new vulnerability has been discovered in macOS Sonoma that is associated with privilege escalation. This vulnerability has been assigned…
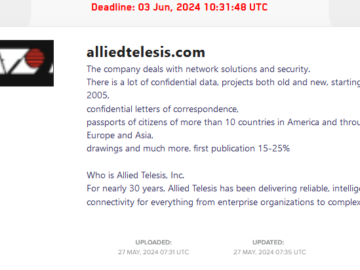
The notorious LockBit has claimed an alleged cyberattack on Allied Telesis, Inc., a prominent American telecommunication equipment supplier. The purported…
WordPress Plugin abused to install e-skimmers in e-commerce sites Pierluigi Paganini May 28, 2024 Threat actors are exploiting a WordPress…
Sav-Rx, a healthcare company based in Fremont, Nebraska, has disclosed a major data breach affecting over 2.8 million individuals, including…
Russian cybercriminals are almost untouchable. For years, hackers based in the country have launched devastating ransomware attacks against hospitals, critical…
The grandeur of Al Habtoor Palace in Dubai set the stage for one of the most significant cybersecurity events in…
The Greek Personal Data Protection Authority (PDPA) has imposed significant fines on the Greek Ministry of Interior and New Democracy…
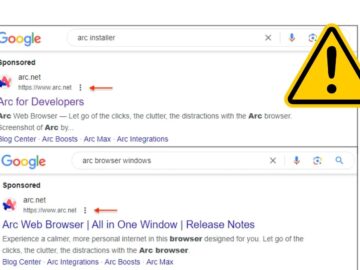
Google Chrome has been the dominant web browser for years now, which is why it may come as a surprise…