24 May 2024 Verizon Data Breach Investigation Report (DBIR) Findings Posted at 08:41h in Blogs by Di Freeze This week…
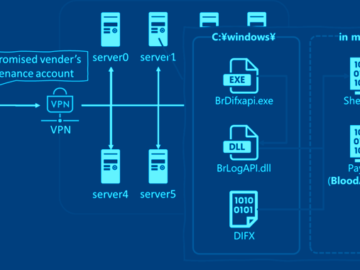
May 24, 2024NewsroomAPT Malware / Cyber Espionage Cybersecurity researchers have discovered that the malware known as BLOODALCHEMY used in attacks…
A vulnerability (CVE-2024-4978) has been identified in JAVS Viewer v8.3.7, a critical component for managing digital recordings in legal and…
Gift cards are attractive to hackers since they provide quick monetization for stolen data or compromised systems. Reselling gift cards…
Russian hackers and APT groups are escalating cyberattacks, leveraging readily available malware and broadening their targets beyond governments. Flashpoint researchers…
May 24, 2024The Hacker NewsCybersecurity Webinar Don’t be fooled into thinking that cyber threats are only a problem for large…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently added a four-year-old security flaw affecting Apache Flink to its…
Japan is creating a consultative body to implement an active cyber defense system to improve its ability to counter cyberattacks…
A new practical and powerful Denial of service attack has been discovered that exploits DNS queries and responses. This new…
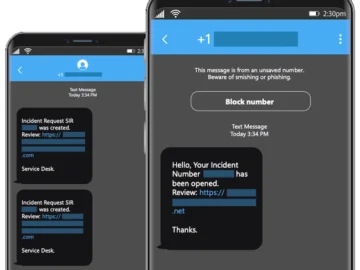
Earlier this month, the FBI published a private industry notification about Storm-0539 (aka Atlas Lion), a Morocco-based cyber criminal group…
May 24, 2024NewsroomVulnerability / Browser Security Google on Thursday rolled out fixes to address a high-severity security flaw in its…
Australian cyber chief announced Friday an “unwelcome development” in the recently disclosed MediSecure data breach. A hacker claimed to possess…