In the ever-evolving landscape of cybersecurity, the need for advanced tools to simulate and test incident response is critical. AttackGen,…
In recent times, the landscape of malware attacks has evolved beyond the traditional encryption tactics followed by ransom demands. A…
Amid the constant drumbeat of successful cyberattacks, some fake data breaches have also cropped up to make sensational headlines. Unfortunately,…
Mar 21, 2024NewsroomVulnerability / Web Security Ivanti has disclosed details of a critical remote code execution flaw impacting Standalone Sentry,…
A 2023 trial of ChatGPT convinced construction heavyweight John Holland Group that it could find a place in its business…
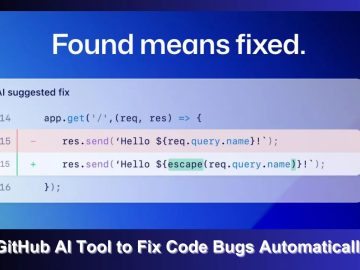
In a groundbreaking move to enhance code security, GitHub has announced the launch of a new feature called “code scanning…
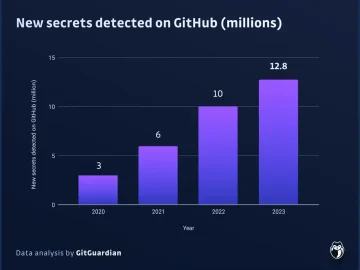
Leaked secrets, a phenomenon known as ‘secrets sprawl,’ is a pervasive vulnerability that plagues nearly every organization. It refers to…
Mar 21, 2024NewsroomDatabase / Vulnerability Atlassian has released patches for more than two dozen security flaws, including a critical bug…
One of the biggest changes in recent times to working life is that going into an office has become optional…
Quality/Effectiveness: Effectiveness measures the method’s ability to provide reliable and accurate vulnerability detections, comprehensive system coverage, compliance with standards, and…
The reason hackers go after financial institutions is because these places have valuable things like money, intellectual property, and sensitive…
It’s not unusual for the data brokers behind people-search websites to use pseudonyms in their day-to-day lives (you would, too)….