Epic Games’ competition lawsuit against Apple and Google has finally opened in the Federal Court, with lawyers kicking off day…
The ongoing “free wedding invite” scam is one of several innovative campaigns aimed at the senior population. Through social media…
The Australian Signals Directorate has added Microsoft threat intelligence into its cyber threat intelligence sharing (CTIS) platform. The directorate said…
Extreme weather events and warnings from experts that keeping temperature rises below the 1.5°C limit is becoming increasingly difficult have…
A former IT support contractor to the Australian National Maritime Museum will spend at least 15 months behind bars over…
A sophisticated hacking campaign attributed to a Chinese Advanced Persistent Threat (APT) group known as ‘Earth Krahang’ has breached 70…
Artificial intelligence (AI) presents the government with opportunities to transform public services, but harnessing the benefits will require a “realistic…
Mike Lynch, the wealthy tech founder once hailed as Britain’s answer to Steve Jobs, oversaw a “multiyear, multilayered fraud” that…
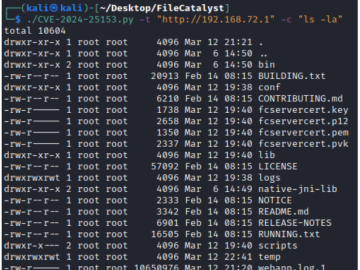
PoC exploit for critical RCE flaw in Fortra FileCatalyst transfer tool released Pierluigi Paganini March 18, 2024 Fortra addressed a…
Image: Midjourney The U.S. Securities and Exchange Commission (SEC) announced today that two investment advisers, Delphia (USA) and Global Predictions,…
Japanese tech giant Fujitsu is investigating a potential data leak after malware infected company systems – This could expose the…
Fujitsu Limited, the largest Japanese IT services provider, has announced that several of the company’s computers have been compromised with…