16 Mar Who’s New On The Cybercrime Magazine Podcast This week in cybersecurity from the editors at Cybercrime Magazine –Listen…
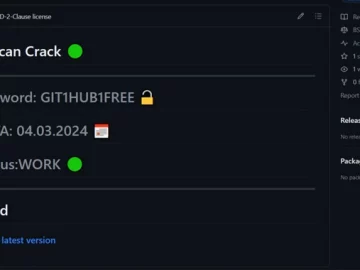
Mar 16, 2024NewsroomMalware / Cybercrime Cybersecurity researchers have found a number of GitHub repositories offering cracked software that are used…
While hunting for bug bounties, attack surface plays a major role. Hacking on mobile adds more juicy attack surface and…
By Rooplakshmi Chamraj, Head HR, Cross Identity In today’s rapidly shifting landscape, finding a harmonious balance between work and personal…
UK-based Sky Betting & Gaming recently launched their own bug bounty program and shared some tips in a blog post:…
Google Chrome has been protecting users from malicious websites and files with Safe Browsing, which maintains a locally-stored list updated…
United States Senator Ron Wyden warned and notified the Director of the National Counterintelligence and Security Center (NCSC), Michael C….
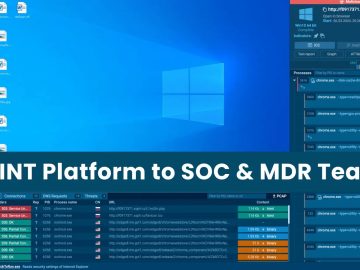
ANY.RUN now integrates with OpenCTI, a cyber threat intelligence platform that allows automatic enrichment of OpenCTI observations with malware data…
The internet is vast and interconnected, but not all are easily accessible through routine browsers and search engines. If we…
Hacktivity proudly showcases the achievements of our hackers and the community, culture, and collaboration we create through the act of…
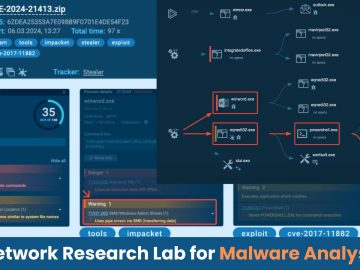
To analyze a security vulnerability (CVE-2024-21413) in Outlook, a controlled environment can be set up using a virtual machine (ANY.RUN)…
The Defense Digital Services (DDS) group is tasked with pioneering private sector solutions to solve some of the Department of…