Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim to shed light…
Following the February 21 attack on Change Healthcare, scores of people in the US have been living with the brutal,…
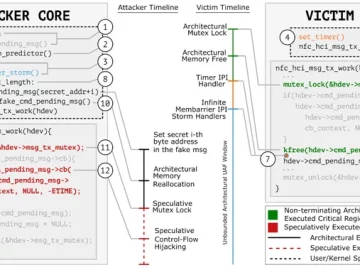
Mar 15, 2024NewsroomHardware Security / Data Protection A group of researchers has discovered a new data leakage attack impacting modern…
The London Mayor’s Office for Policing and Crime (Mopac), which oversees London’s Metropolitan Police Force, has been reprimanded by the…
To reflect this, we’re changing our hiring practices – we no longer require a bachelor’s degree on most job descriptions….
The U.S. Department of Justice (DoJ) is recovering $2.3 million worth of cryptocurrency linked to a “pig butchering” fraud scheme…
Comforte AG and ACI Worldwide have announced a partnership together to accelerate payment modernisation with global PCI DSS v4.0 Compliance….
A bill introduced by senators Dick Durbin and Mike Lee to reauthorize the Section 702 surveillance program is the fifth…
New high-performance malware “BunnyLoader 3.0” steals logins, crypto & lurks undetected. Palo Alto Unit 42 reveals its tricks to help…
For those prioritizing a secure browsing experience, here’s some promising news: Google has announced that Chrome users utilizing the safe…
Tools such as Open AI’s DALL.E 2, SORA and Chat GPT, Google’s Bard (now Gemini), and Microsoft’s Copilot, now make…
Moldovan national Sandu Boris Diaconu has been sentenced to 42 months in prison for operating E-Root, a major online marketplace…