A new variant of StopCrypt ransomware (aka STOP) was spotted in the wild, employing a multi-stage execution process that involves…
AI tech fuels surge in financial fraud and cybercrime, warns INTERPOL. Sophisticated scams and human trafficking rings exploit cryptocurrency and…
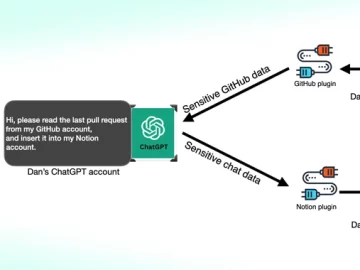
Mar 15, 2024NewsroomData Privacy / Artificial Intelligence Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act…
A threat actor has surfaced on the dark web, announcing the creation of “Hell Paradise,” a covert online platform purportedly…
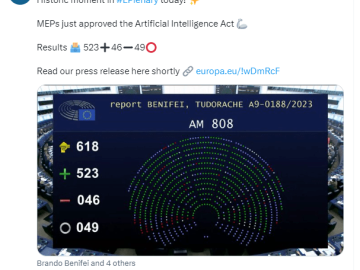
The European Parliament has approved the groundbreaking Artificial Intelligence (AI) Act, signaling a pivotal step towards regulating AI technologies while…
The cybersecurity landscape has been shaken by the discovery that a single piece of malware, known as RedLine, has stolen…
A massive data breach at a French employment agency is affecting over 43 million users – representing more than half…
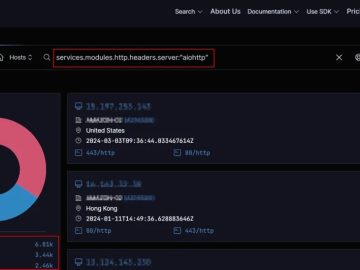
In the final week of January 2024, CGSI (Cyble Global Sensor Intelligence) uncovered a potential exploitation of an Aiohttp vulnerability…
Venmo, a mobile payment service owned by PayPal, has become a household name in the United States. It facilitates a…
Today, Eskenzi PR are proud to announce that nominations are open for the 11th annual European Cybersecurity Bloggers Awards. The…
Google has announced an upgrade to its Safe Browsing technology to provide Chrome users with real-time protection against phishing, malware,…
Cyber threats are growing at an unprecedented pace, and the year ahead is fraught with cybercrime and incidents anticipated ahead…