A massive data leak (585.81 GB) exposed customer information at Qmerit, including home images, charger locations, and potentially more –…
13 Mar Smartphone Owners Warned Over “AI Tsunami,” Advised To Use Passkeys This week in cybersecurity from the editors at…
For its 2024 second-quarter filing, Nutanix reported revenue of $525m, with annual contract value rising 23% to $330m, while recurring revenue…
In today’s hyper-connected digital world, cyber threats are more prevalent than ever, with cyberattacks occurring every 39 seconds on average,…
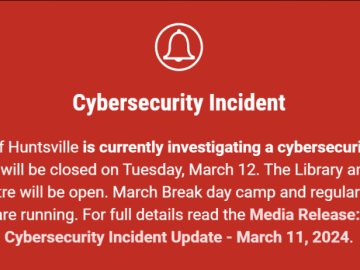
Residents of Huntsville, Ontario, woke up to unsettling news as the town grappled with the aftermath of a cyberattack over…
Acer Philippines disclosed a data breach after a third-party vendor hack Pierluigi Paganini March 13, 2024 Acer Philippines disclosed a…
Russian-Canadian cybercriminal Mikhail Vasiliev has been sentenced to four years in prison by an Ontario court for his involvement in…
WIRED collaborated with Der Spiegel, Recorder, and The Washington Post on this reporting. Each wrote separate stories that the news…
Threat actors use malicious PyPI packages to infiltrate systems and execute various attacks like data exfiltration, ransomware deployment, or system…
Mar 13, 2024NewsroomLarge Language Model / AI Security Google’s Gemini large language model (LLM) is susceptible to security threats that…
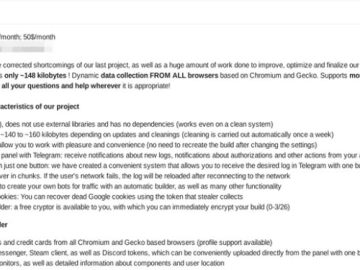
A new information stealer has entered the dark web markets. Dubbed “Xehook Stealer,” this .NET-based malware, meticulously crafted to target…
Microsoft published its March 2024 Patch Tuesday, which addressed almost 59 vulnerabilities in its products and none of them were…