Blockchains lack true randomness, hindering applications like fair games, DeFi, and NFTs. Pyth Network’s “Pyth Entropy” solves this with provably…
12 Mar AI-Generated Articles And The Media. Thoughts From Cybercrime Magazine. This week in cybersecurity from the editors at Cybercrime…
The UK government has signed a science and research agreement with Germany to collaborate on joint opportunities in areas such…
French government services have been hit by cyberattacks of “unprecedented intensity,” according to reports from multiple media sources. Prime Minister…
Join us for an interview with Darren Thomson, Field Chief Technology Officer at Commvault, as we delve into the dynamic…
Leicester City Council grapples with a cyber attack, causing major disruption to residents. IT systems and phone lines remain down…
Mar 12, 2024The Hacker NewsCryptocurrency / Cybercrime Threat hunters have discovered a set of seven packages on the Python Package…
Apart from ChatGPT and Gemini AI which are the most popular Artificial Intelligence systems available to the public, there are…
CloudGrappler is an innovative open-source tool designed to detect the presence of notorious threat actors in cloud environments. This tool…
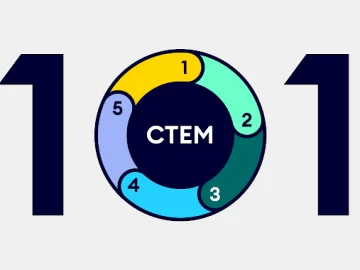
Mar 12, 2024The Hacker NewsCTEM / Vulnerability Management In a world of ever-expanding jargon, adding another FLA (Four-Letter Acronym) to…
Current figures on subpostmaster accounting shortfalls put into perspective the Post Office’s “staggering mismanagement” of discrepancies experienced by those operating…
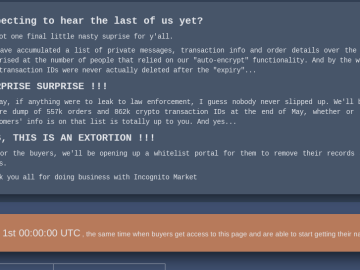
Hidden marketplaces on the dark web have long been a staple for those seeking to engage in illicit transactions. Since…