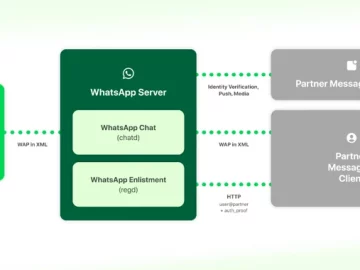
Mar 08, 2024NewsroomInteroperability / Encryption Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger…
The Massachusetts Institute of Technology’s (MITRE) Aviation Risk Identification and Assessment (ARIA) software program is a powerful tool to enhance…
JetBrains issued a warning on March 4, 2024 about two serious vulnerabilities in TeamCity server. The flaws can be used…
By Zinet Kemal, Associate Cloud Security Engineer, Best Buy The cybersecurity space, as dynamic and challenging as it is, has…
Henry Onyedikachi Echefu, a 32-year-old Nigerian national, has admitted to his role in a sophisticated business email compromise (BEC) scheme…
Cybersecurity researchers at ESET identified the cyberespionage campaign, highlighting how hackers compromised both the Tibetan news website Tibetpost and the…
Mar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at…
GitLab has announced the release of updated versions for its Community Edition (CE) and Enterprise Edition (EE) platforms. These updates…
International Women’s Day has long been an advocate for elevating and advancing gender equality within the technology industry. At the…
Cisco has fixed two high-severity vulnerabilities affecting its Cisco Secure Client enterprise VPN and endpoint security solution, one of which…
The Coper malware, a descendant of the Exobot malware family, was first distributed as a fake version of Bancolombia’s ‘Personas’…
By Jasmine Harrison PC.dp, Account Manager – Data Protection People Women play an important role in the field of data…