Evasive Panda dubbed BRONZE HIGHLAND and Daggerfly, a Chinese-speaking APT group operating since at least 2012, has been spotted conducting cyberespionage…
CrowdStrike announced its acquisition of Flow Security, the industry’s first cloud-native data runtime security solution. This move positions CrowdStrike as…
Threat actors target email addresses, as they provide a way to access personal and confidential information. Emails often hold valuable…
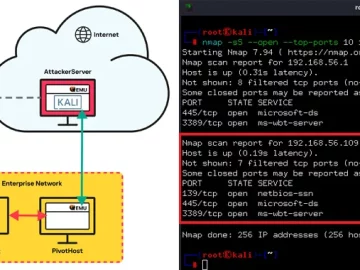
Mar 08, 2024NewsroomEndpoint Security / Network Security Threat actors have been observed leveraging the QEMU open-source hardware emulator as tunneling…
In the fast-paced world of cybersecurity, diversity isn’t just a buzzword; it’s a necessity for success. Yet, the door to…
Play ransomware attack on Xplain exposed 65,000 files containing data relevant to the Swiss Federal Administration. Pierluigi Paganini March 08,…
The end-of-life for Talos rules support for two versions of the widespread intrusion detection and prevention system Snort has been…
Mar 08, 2024NewsroomNetwork Security / Vulnerability Cisco has released patches to address a high-severity security flaw impacting its Secure Client…
The frequency of malicious emails successfully circumventing Secure Email Gateways (SEGs) has doubled in the past year. This surge highlights the evolving sophistication of cyber threats and the challenges organizations face in…
Security leaders recognize that the pattern of buying new tech and the frantic state of find-fix vulnerability management is not…
Federal Bureau of Investigation (FBI) has published its annual Internet Crime Report for 2023, highlighting a significant 22% increase in…
We’re almost at our third Patch Tuesday and wrapping up the first quarter 2024. Time flies by! Microsoft is starting…