98% of companies surveyed view some of their AI models as vital for business success, and 77% have experienced breaches…
Mar 07, 2024NewsroomMalware / Network Security Threat actors have been leveraging fake websites advertising popular video conferencing software such as…
WordPress, a widely used content management system that powers millions of websites around the world, has become a source of…
Cisco is warning that Webex and Jabber on Android will lose the ability to receive calls or messages from various…
FINTRAC Canada targeted by a cyber attack FINTRAC, Canada’s financial intelligence agency, has fallen victim to a cyber attack, prompting…
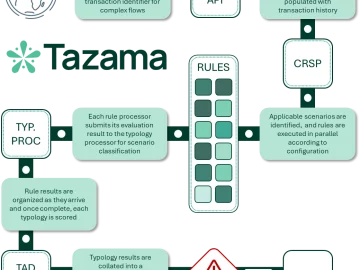
Tazama is an open-source platform focused on improving fraud management within digital payment systems. Tazama marks a substantial transformation in…
Cybersecurity remained a top priority and an area of growth for MSPs, with 73% saying it’s a top revenue driver…
Ransomware attacks remain a formidable challenge for organizations worldwide. These attacks not only encrypt critical data, rendering it inaccessible to…
The darknet is home to many underground hacking forums in which cybercriminals convene, freely sharing stories, tactics, success stories and…
Cybersecurity experts at Cleafy Labs have exposed a sophisticated fraud campaign orchestrated by a group known as Copybara. This campaign,…
Apple releases emergency fixes to address two new zero-day vulnerabilities in iOS that impact iPhones. The two zero-day vulnerabilities were…
The threat actor, who goes by the name “z0miner,” has been found to be attacking Korean WebLogic servers to distribute…