LockBit 3.0’s Bungled Comeback Highlights the Undying Risk of Torrent-Based (P2P) Data Leakage Pierluigi Paganini March 06, 2024 The wide…
A hacking group has evolved with a new ransomware variant known as GhostLocker 2.0. This group, in collaboration with the…
Hackers use weaponized calendar invites to exploit vulnerabilities in email systems, tricking users into clicking on malicious links or downloading…
Mar 06, 2024NewsroomPrivacy / Spyware The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) sanctioned two individuals and…
The Post Office’s decision to prosecute subpostmasters using Horizon evidence during the software’s early roll-out phase was “frightening”, according to…
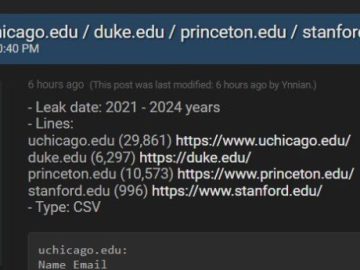
A hacker operating on the dark web has asserted possession of data from prestigious educational institutions in the United States….
Malware can use the Notepad service to attack systems such as Windows and Linux since Notepad is a widely used…
A threat actor has been identified as creating fraudulent Skype, Google Meet, and Zoom websites to distribute malware, explicitly targeting…
The cybercrime group called GhostSec has been linked to a Golang variant of a ransomware family called GhostLocker. “TheGhostSec and…
Hackers launch large-scale DDoS attacks to disrupt and make online services inaccessible, driven by motives like revenge or protest, flooding…
Shortly after millions of Facebook and Instagram users encountered difficulties accessing their accounts, speculation quickly arose that a state-funded cyberattack…
Data loss from insiders continues to pose a growing threat to security, with emerging technologies such as AI and generative…