Microsoft says that systems running Windows 11 22H2 will continue to receive non-security preview updates after initially stating they would…
29 Feb A Discussion with Michael Hamilton, Founder of Critical Insight, and Stephen Salinas, Stellar Cyber The latest trends, challenges,…
CVE-2024-1553 and CVE-2024-1557 are memory-safety bugs rated as having a high severity. “Some of these bugs showed evidence of memory…
Infoblox cybersecurity researchers are warning users about a fraudulent scheme launched by a DNS threat actor Savvy Seahorse, which uses…
29 Feb NIST Cybersecurity Framework 2.0 and the SaaS Stack Posted at 11:48h in Blogs by Di Freeze The long-awaited…
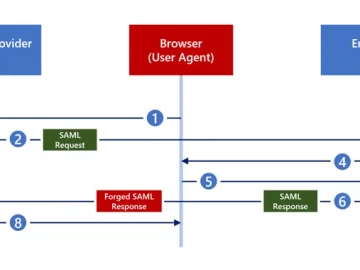
Feb 29, 2024NewsroomThreat Intelligence / Cyber Threat Cybersecurity researchers have disclosed a new attack technique called Silver SAML that can…
AI service Cutout.Pro has suffered a data breach exposing the personal information of 20 million members, including email addresses, hashed…
While both serve similar purposes, there are specific differences between residential proxies and VPNs that users should understand to make…
Data security concerns with Chinese and other nation cars The security of data in cars from China and other nations…
Identity and access management (IAM) provider Okta has announced it is to double its investment in security over the next…
In cybersecurity, information is what ultimately makes it possible to respond to threats effectively and proactively. One of the most…
29 Feb USA Today’s Cybersecurity Statistics In 2024 This week in cybersecurity from the editors at Cybercrime Magazine – Read…