In a recent wave of cyberattacks on cryptocurrency enthusiasts, malicious actors have been employing sophisticated tactics to infiltrate macOS systems….
Lazarus APT exploited zero-day in Windows driver to gain kernel privileges Pierluigi Paganini February 29, 2024 North Korea-linked Lazarus APT…
Image: Midjourney A threat actor named Savvy Seahorse is abusing CNAME DNS records Domain Name System to create a traffic…
Security researchers have uncovered a massive campaign of repository confusion attacks on GitHub, affecting over 100,000 repositories and potentially millions…
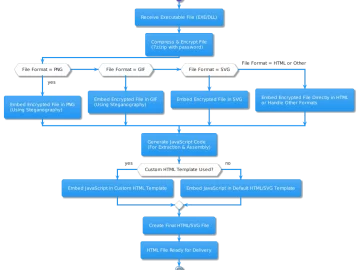
BobTheSmuggler is an open-source tool designed to easily compress, encrypt, and securely transport your payload. It basically enables you to…
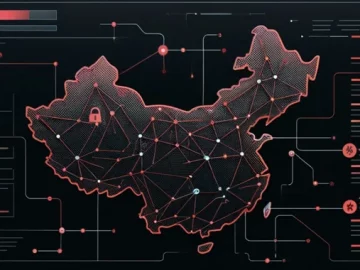
At least two different suspected China-linked cyber espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the exploitation…
These days, cyber threat actors continue to rely just as much on psychological manipulation in the form of convincing phishing…
The Lazarus Group, a well-known cybercriminal organization, has recently exploited a zero-day vulnerability in Windows to gain kernel privileges, a…
For years, IT experts have emphasized the importance of maintaining backups for data and applications, highlighting their crucial role in…
As commercial adoption of cloud technologies continues, cloud-focused malware campaigns have increased in sophistication and number – a collective effort…
U.S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens’ personal data to countries…
North Korean threat actors known as the Lazarus Group exploited a flaw in the Windows AppLocker driver (appid.sys) as a…