Kali Linux has released version 2024.1, the first version of 2024, with four new tools, a theme refresh, and desktop…
By Luke Wallace, VP of Engineering at Bottle Rocket With rising oil prices, higher interest rates, and an economic downturn…
US president Joe Biden will sign an executive order on Wednesday aimed at preventing a handful of countries, including China,…
The Predator Files project, coordinated by the European Investigative Collaborations (EIC), has highlighted the extensive use of Predator spyware by…
In an updated #StopRansomware security advisory, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and…
Approximately 75% of all recorded cyber security breaches that originated through a third-party occurred after other entities in the victim’s…
The LockBit ransomware gang is once again conducting attacks, using updated encryptors with ransom notes linking to new servers after…
The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human…
By Zac Amos, Features Editor, ReHack Cyberattacks are a growing problem worldwide as they can cause significant damage to any…
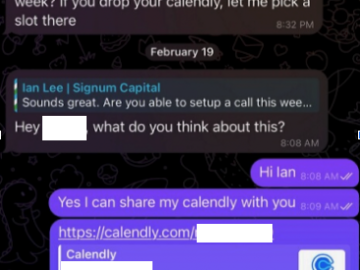
Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s…
To raise awareness of the ALPHV Blackcat ransomware as a service (RaaS) that targets the US healthcare industry, the FBI, CISA,…
28 Feb Freelance TV Presenter Paid To Pose As A Crypto CEO. Millions Lost In The Hyperverse Scam. This week…