Advanced Persistent Threat (APT) group known as ToddyCat, new insights have emerged regarding their sophisticated methods of hijacking network infrastructure to steal sensitive data from governmental organizations across the Asia-Pacific region. This…
APT29, a Russian threat group, targeted German political parties with a new backdoor called WINELOADER using spear-phishing emails containing malicious…
Large language models (LLMs) have achieved superhuman performance on many benchmarks, leading to a surge of interest in LLM agents…
By: Rajat Kohli, Partner at Zinnov There is something to be learned from epic fantasy productions like Harry Potter. That…
Hackers often target PyPI packages to exploit vulnerabilities and inject malicious code into widely used Python libraries. Recently, cybersecurity researchers…
Since the initial disclosure of 15 vulnerabilities in November 2023, a 220% increase in vulnerabilities impacting AI systems has been…
Anonymous claims a successful cyberattack against the Israeli Defence Force (IDF), gaining access to 20 gigabytes of data, which allegedly…
Hackers threaten to leak a copy of the World-Check database used to assess potential risks associated with entities Pierluigi Paganini…
Wallarm introduced its ongoing Open Source API Firewall project to the world at the recently concluded Blackhat Asia 2024 conference…
A new supply-chain vulnerability has been identified in the Lambda Layers of third-party TensorFlow-based Keras models. This vulnerability could allow…
22 Apr 5 Cybersecurity Questions Boards Can’t Afford To Ignore Posted at 08:49h in Blogs by Di Freeze This week…
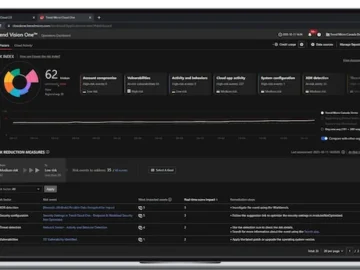
Trend Micro unveiled AI-driven cyber risk management capabilities across its entire flagship platform, Trend Vision One. This seamlessly integrates more…